What is Reconciliation
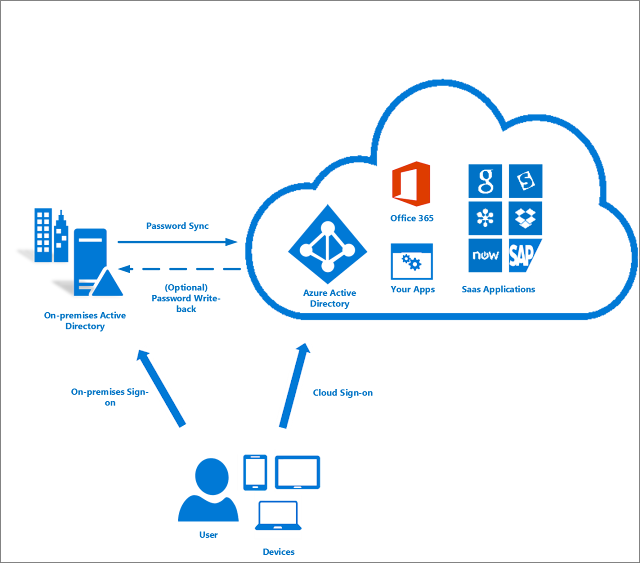
What is Reconciliation in Identity Management Reconciliation is a term used in Identity Management for recognizing changes to Identity attributes and their subsequent synchronization with other user stores or an Identity Manager. Identity Manager is a product (e.g. Oracle Identity Manager, SailPoint IIQ Identity Manager) that provides full view and management of user's Life cycle, from creating an account to its final disablement or management of user account on-boarding, off-boarding or user provisioning/de-provisioning. Here User on-boarding/off-boarding is in terms of Business Processes whereas provisioning/de-provisioning is in terms of technical steps. Reconciliation or "Recon" is a generic term used for various Identity Management products, such as Oracle Identity Manager, SailPoint IIQ, IBM Security Identity Manager. Here is how Oracle defines Reconciliation: When changes in the identities are made directly in a user store, for example an LDAP identity store,...