What is HSTS - HTTP Strict Transport Security
HSTS stands for HTTP Strict Transport Security. In essence it is actually a mitigation technique for SSL-Stripping attack. In practice one may encounter message when accessing websites (see below details)
Various attacks attempt to remove the use of Secure Socket Layer/Transport Layer Security (SSL/TLS) altogether by modifying unencrypted protocols that request the use of TLS, specifically modifying HTTP traffic and HTML pages as they pass on the wire. These attacks are known collectively as "SSL Stripping" (a form of the more generic "downgrade attack") and were first introduced by Moxie Marlinspike [SSL-Stripping]. In the context of Web traffic, these attacks are only effective if the client initially accesses a Web server using HTTP. A commonly used mitigation is HTTP Strict Transport Security (HSTS) [RFC6797].
HSTS is now supported in all leading browsers - Chrome, Firefox, Safari, Edge, IE.
One of the several new features in Chrome is the addition of HTTP Strict Transport Security. HSTS allows a site to request that it always be contacted over HTTPS. HSTS is supported in Google Chrome, Firefox, Safari, Opera, Edge and IE (caniuse.com has a compatibility matrix).
What issue does HSTS address?
The issue that HSTS addresses is that users tend to type http:// and omit the scheme entirely most of the time. In the latter case, browsers will insert http:// for them.
However, HTTP is insecure. An attacker can grab that connection, manipulate it and only the most eagle eyed users might notice that it redirected to https://www.bank0famerica.com or some such. From then on, the user is under the control of the attacker, who can intercept passwords etc at will.
An HSTS enabled server (or site aka website) can include the following header in an HTTPS reply:
Strict-Transport-Security: max-age=16070400; includeSubDomains
When the browser sees this, it will remember, for the given number of seconds, that the current domain should only be contacted over HTTPS. In the future, if the user types http:// or omits the scheme, HTTPS is the default. (in other words http will not be allowed even if user typed http://) In fact, all requests for URLs in the current domain will be redirected to HTTPS. (So you have to make sure that you can serve them all!).
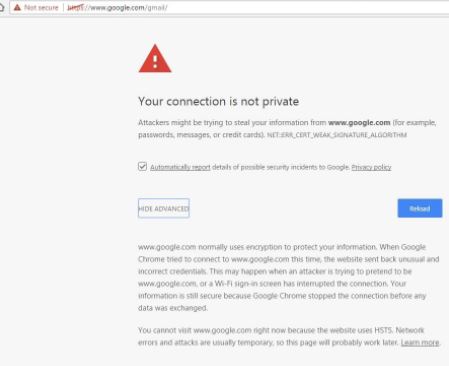
On a different note, in practice one may encounter the message about HSTS when accessing websites for testing or any other similar purpose where you do actually need to use http. Below is use case encountered with HSTS. If you are getting this error "Your website uses HSTS" when you are trying to access a website then it means that the browser has blocked access to this website.
HSTS stands for HTTP Strict Transport Security.
You can can get past this error by manually turning off the HSTS setting in your browser for the particular website. This is a security feature to prevent from using HTTP instead of HTTPS and also mitigate a MITM attack (man in the middle). In fact browsers, such as chrome and mozilla come preloaded with websites which require HSTS.
However, there could be cases when you may require to turn off this setting. Why would one want to turn off this setting? It is good to have this security feature available so users continue to use the HTTPS (not drop to plain HTTP). I got this error when using a local proxy to access a website. It was a genuine case where I needed to access the website and was being prevented (the HSTS security setting in the browser prevented from accessing this site). Hence the need to turn off this feature so as to be able to access the website.
Once the local proxy settings was removed I could access the site fine. However, I did require to use the local proxy setting for my use case, so removing the proxy setting was not an acceptable solution. Hence the only other solution was to turn off the HSTS setting for this particular site.
I got this error when using the Apache JMeter HTTPS Test Script Recorder. This requires to configure your browser/chrome with Proxy settings. The HTTPS Test Script Recorder enables a proxy that is used to record all the HTTP/HTTPS traffic within JMeter. For this JMeter generates a X509 certificate which is to be installed in your browser.
However, this creates issue when accessing the website, since the certificate presented by the browser is issued by Jmeter. And consequently the site will be unreachable with below errors.
See below how to check the current HSTS settings from chrome browser. With this chrome feature you can check which websites or domains have the HSTS turned on. You can also turn off HSTS for a website using this feature.
How to check HSTS settings in chrome browser.
Open chrome browser and enter this URL chrome://net-internals/#hsts
You will get below screen
See below screenshot (it is same as above, but only showing the Query section), you can check for google.com domain, for example. The query (enter your domain name, next to the Domain info box and click Query), shows that HSTS is turned on for this domain- as it is reporting Found as shown in the screenshot.
Now if you want to turn this feature off, then again use this Delete option as shown below (Note, this Delete option is below in the same page)
In the above field for Domain, enter the name of the domain for which you want this feature/HSTS to be turned off and click Delete button.
Once you have done this, you can go back to the Query field and check if the domain was removed. The Query now should give you Not found (as shown below). Compare with similar Query shown above which gave a list as output, now it the output is nil, says "Not found" (compare below screen shot of Query HSTS with above screenshot for Query HSTS)
Now your browser will not prevent you from accessing this website. In my use case, once HSTS feature was turned off in the chrome browser, (by following the steps above by Delete action) the website was accessible again.
However, note that the browser comes preloaded with entries for HSTS feature and these cannot be deleted using the Delete button.
Note: (1) HSTS is specified in RFC 6797
(2) Chrome has discontinued the net-internal URL, chrome://net-internals. See below when you attempt to access chrome://net-internals directly
So if you are interested in using HSTS then provide the full URL as chrome://net-internals/#hsts
Also this site is a good reference for HSTS in general
Various attacks attempt to remove the use of Secure Socket Layer/Transport Layer Security (SSL/TLS) altogether by modifying unencrypted protocols that request the use of TLS, specifically modifying HTTP traffic and HTML pages as they pass on the wire. These attacks are known collectively as "SSL Stripping" (a form of the more generic "downgrade attack") and were first introduced by Moxie Marlinspike [SSL-Stripping]. In the context of Web traffic, these attacks are only effective if the client initially accesses a Web server using HTTP. A commonly used mitigation is HTTP Strict Transport Security (HSTS) [RFC6797].
HSTS is now supported in all leading browsers - Chrome, Firefox, Safari, Edge, IE.
One of the several new features in Chrome is the addition of HTTP Strict Transport Security. HSTS allows a site to request that it always be contacted over HTTPS. HSTS is supported in Google Chrome, Firefox, Safari, Opera, Edge and IE (caniuse.com has a compatibility matrix).
What issue does HSTS address?
The issue that HSTS addresses is that users tend to type http:// and omit the scheme entirely most of the time. In the latter case, browsers will insert http:// for them.
However, HTTP is insecure. An attacker can grab that connection, manipulate it and only the most eagle eyed users might notice that it redirected to https://www.bank0famerica.com or some such. From then on, the user is under the control of the attacker, who can intercept passwords etc at will.
An HSTS enabled server (or site aka website) can include the following header in an HTTPS reply:
Strict-Transport-Security: max-age=16070400; includeSubDomains
When the browser sees this, it will remember, for the given number of seconds, that the current domain should only be contacted over HTTPS. In the future, if the user types http:// or omits the scheme, HTTPS is the default. (in other words http will not be allowed even if user typed http://) In fact, all requests for URLs in the current domain will be redirected to HTTPS. (So you have to make sure that you can serve them all!).
On a different note, in practice one may encounter the message about HSTS when accessing websites for testing or any other similar purpose where you do actually need to use http. Below is use case encountered with HSTS. If you are getting this error "Your website uses HSTS" when you are trying to access a website then it means that the browser has blocked access to this website.
You can can get past this error by manually turning off the HSTS setting in your browser for the particular website. This is a security feature to prevent from using HTTP instead of HTTPS and also mitigate a MITM attack (man in the middle). In fact browsers, such as chrome and mozilla come preloaded with websites which require HSTS.
However, there could be cases when you may require to turn off this setting. Why would one want to turn off this setting? It is good to have this security feature available so users continue to use the HTTPS (not drop to plain HTTP). I got this error when using a local proxy to access a website. It was a genuine case where I needed to access the website and was being prevented (the HSTS security setting in the browser prevented from accessing this site). Hence the need to turn off this feature so as to be able to access the website.
Once the local proxy settings was removed I could access the site fine. However, I did require to use the local proxy setting for my use case, so removing the proxy setting was not an acceptable solution. Hence the only other solution was to turn off the HSTS setting for this particular site.
I got this error when using the Apache JMeter HTTPS Test Script Recorder. This requires to configure your browser/chrome with Proxy settings. The HTTPS Test Script Recorder enables a proxy that is used to record all the HTTP/HTTPS traffic within JMeter. For this JMeter generates a X509 certificate which is to be installed in your browser.
However, this creates issue when accessing the website, since the certificate presented by the browser is issued by Jmeter. And consequently the site will be unreachable with below errors.
See below how to check the current HSTS settings from chrome browser. With this chrome feature you can check which websites or domains have the HSTS turned on. You can also turn off HSTS for a website using this feature.
How to check HSTS settings in chrome browser.
Open chrome browser and enter this URL chrome://net-internals/#hsts
You will get below screen
See below screenshot (it is same as above, but only showing the Query section), you can check for google.com domain, for example. The query (enter your domain name, next to the Domain info box and click Query), shows that HSTS is turned on for this domain- as it is reporting Found as shown in the screenshot.
 |
| Query HSTS |
Now if you want to turn this feature off, then again use this Delete option as shown below (Note, this Delete option is below in the same page)
 |
| Delete domain |
In the above field for Domain, enter the name of the domain for which you want this feature/HSTS to be turned off and click Delete button.
Once you have done this, you can go back to the Query field and check if the domain was removed. The Query now should give you Not found (as shown below). Compare with similar Query shown above which gave a list as output, now it the output is nil, says "Not found" (compare below screen shot of Query HSTS with above screenshot for Query HSTS)
 |
| Query HSTS |
Now your browser will not prevent you from accessing this website. In my use case, once HSTS feature was turned off in the chrome browser, (by following the steps above by Delete action) the website was accessible again.
However, note that the browser comes preloaded with entries for HSTS feature and these cannot be deleted using the Delete button.
Note: (1) HSTS is specified in RFC 6797
(2) Chrome has discontinued the net-internal URL, chrome://net-internals. See below when you attempt to access chrome://net-internals directly
So if you are interested in using HSTS then provide the full URL as chrome://net-internals/#hsts
Also this site is a good reference for HSTS in general





Comments
Post a Comment