Getting started with Dockers
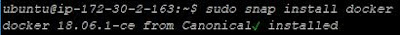
This post will cover the steps required to get Docker installed on Linux host (RHEL Red Hat Enterprise Linux). In essence when we say, installing Docker, it means installing a Docker engine. Why would one want to install a Docker engine? It is for making containers exist on an Operating system. After Docker (engine) is installed on the Operating System, then you can run applications in the docker container. One installs a Docker engine on the Operating System. Next, you create a Docker image. The Docker engine will allow to run individual containers from the Docker image. Put simply a container is a runtime instance of the Docker image. A docker container is a process which runs on a host. Docker or rather the Docker engine enables these processes to run in isolated containers. In other words, Docker makes possible or enables to create, run and manage containers on a single operating system. A Docker container contains all the application and its dependencies, thereby one can safely