Oracle Mobile and Social OMSS
OMSS Oracle Mobile and Social Service
What is Oracle OMSS? Oracle Mobile and Social Service also called Oracle M&S is the OAM 11gR2PS3 version. Prior to version 11.1.2.3, Mobile and Social Services was named Mobile Services.
OMSS provides two things - Mobile Services and Social Identity services
Mobile Services connects applications and devices to the enterprise Access Management and Identity Management services available in the Oracle Identity Access Management product suite. This makes it easy to utilize sophisticated authentication and authorization services functionality (such as mobile device and application registration, and device fingerprinting) to restrict access to authorized devices only. Client applications can also implement knowledge-based authentication, a powerful feature that goes beyond basic password-based authentication.
Mobile Services can be configured to require a valid device and client credential and a User Token with each application token request. This ensures that only an authorized user can access a protected resource, and then only if the user is running an authorized application on an authorized device. Mobile Services also provides easy access to User Profile Services if Mobile and Social is integrated with an LDAP compliant directory server.
Social Identity allows Mobile and Social to serve as the relying party when interacting with popular cloud-based identity authentication and authorization services, such as Google, Yahoo, Facebook, Foursquare, Windows Live, Twitter, and/or LinkedIn. After deploying Mobile and Social, a user is provided with multiple log-in options without the need to implement each provider individually. This allows users to access protected resources using their credentials from a trusted Identity Provider.
Oracle case study with sample application protected by OMSS
In addition to tight integration with Access Manager, Mobile and Social is "pre-wired" to work with other back-end Identity and Access Management Service offerings, including Oracle Adaptive Access Manager (OAAM) and a variety of LDAP compliant directory servers. On the front-end, Mobile and Social provides easy to use SDKs for integration of client applications on the Java, Android, and iOS platforms. The client applications then use simple REST calls to communicate with the Mobile and Social server.
Oracle community discussion on OMSS
Oracle Mobile and Social Service in the OAM console

The authentication steps show how OAM acts as the Relying Party and the remote authentication provider (e.g. Google, Facebook, Linkedin, Twitter, ) acts as the Identity Provider. This requires that the Identity Provider configuration is pre-configured in the OAM (OMSS) and accepts the auth token provided by the IDP and generates another token. (See this post in fusionsecurity blog)
The above use case is similar to the Federation use case with OAM being the Service Provider.
Refer the OAM documentation on OMSS
What is Oracle OMSS? Oracle Mobile and Social Service also called Oracle M&S is the OAM 11gR2PS3 version. Prior to version 11.1.2.3, Mobile and Social Services was named Mobile Services.
OMSS provides two things - Mobile Services and Social Identity services
Mobile Services connects applications and devices to the enterprise Access Management and Identity Management services available in the Oracle Identity Access Management product suite. This makes it easy to utilize sophisticated authentication and authorization services functionality (such as mobile device and application registration, and device fingerprinting) to restrict access to authorized devices only. Client applications can also implement knowledge-based authentication, a powerful feature that goes beyond basic password-based authentication.
Mobile Services can be configured to require a valid device and client credential and a User Token with each application token request. This ensures that only an authorized user can access a protected resource, and then only if the user is running an authorized application on an authorized device. Mobile Services also provides easy access to User Profile Services if Mobile and Social is integrated with an LDAP compliant directory server.
Social Identity allows Mobile and Social to serve as the relying party when interacting with popular cloud-based identity authentication and authorization services, such as Google, Yahoo, Facebook, Foursquare, Windows Live, Twitter, and/or LinkedIn. After deploying Mobile and Social, a user is provided with multiple log-in options without the need to implement each provider individually. This allows users to access protected resources using their credentials from a trusted Identity Provider.
Oracle case study with sample application protected by OMSS
In addition to tight integration with Access Manager, Mobile and Social is "pre-wired" to work with other back-end Identity and Access Management Service offerings, including Oracle Adaptive Access Manager (OAAM) and a variety of LDAP compliant directory servers. On the front-end, Mobile and Social provides easy to use SDKs for integration of client applications on the Java, Android, and iOS platforms. The client applications then use simple REST calls to communicate with the Mobile and Social server.
Oracle community discussion on OMSS
Oracle Mobile and Social Service in the OAM console

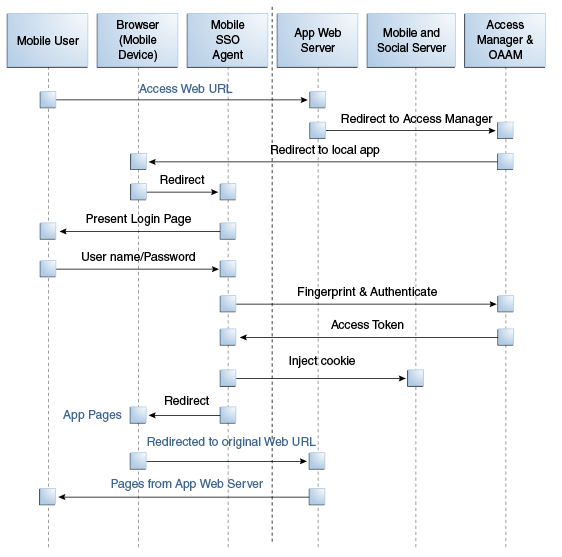
Authentication Flow Sequence Diagram
The authentication steps show how OAM acts as the Relying Party and the remote authentication provider (e.g. Google, Facebook, Linkedin, Twitter, ) acts as the Identity Provider. This requires that the Identity Provider configuration is pre-configured in the OAM (OMSS) and accepts the auth token provided by the IDP and generates another token. (See this post in fusionsecurity blog)
The above use case is similar to the Federation use case with OAM being the Service Provider.
Refer the OAM documentation on OMSS

Authenticating user from a browser based Web App from a registered mobile device



Comments
Post a Comment