OAM authentication with WebLogic server
This post provides the flow and steps for Oracle Access Manager (OAM) integration with Oracle WebLogic server - this is the integration of OAM with any protected application deployed on Web Logic server. This pattern is followed for all Oracle Fusion Middleware products (Oracle Identity Manager, Oracle SOA Suite, or Oracle Web Center etc) authentication with OAM. This is the core of how Single sign on works with Oracle Access Manager. The two important ingredients that make the sso happen are the OAM_REMOTE_USER Http Header and the OAMAuthen cookie. Http is the medium of transfer of data flow between all the components here - OAM, WebGate, WebLogic server, Application and lastly the user's browser. The user authentication information is carried in the Http Header. In essence, OAM authenticates a user to an application deployed on the WebLogic server using the Identity Asserter function. Below is the steps in this process (LINK to Oracle doc)
Here is a high level overview which shows User trying to access protected resource, other components are Access Manager Server and Admin server with their backend policy store. For detailed steps see further below.
 |
| OAM High Level Overview |
1) A user attempts to access an OAM protected Web application that is deployed on the Oracle WebLogic Server.
2) WebGate on a reverse proxy Web server intercepts the request and queries the OAM Server to determine whether the requested resource is protected. (This reverse proxy server for example can be a OHS server with mod wls routing configuration). Additionally WebGate is also installed on the OHS server. This completes the step2 pre-requisites.
3) If the requested resource is protected, WebGate challenges the user for credentials based on the type of OAM authentication scheme configured for the resource (Oracle recommends Form Login). The user presents credentials such as user name and password.
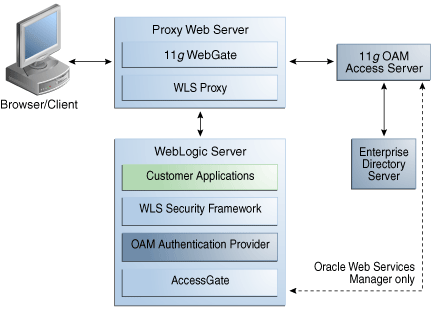 |
| Identity Asserter Configuration with Oracle Access Manager and WebGates |
4) WebGate forwards the authentication request to the OAM Server.
5) OAM 11g Server validates user credentials against the primary user identity store and returns the response to WebGate (OAM 10g/11g Access Server validates user credentials against configured user directories). Upon:
Successful Authentication: Processing continues with Step 6.
Authentication Not Successful: The login form appears asking the user for credentials again; no error is reported.
6) OAM Server generates the session token and sends it to the WebGate:
11g WebGate: Sets and returns the OAMAuthn cookie and triggers the OAM_REMOTE_USER (or OAM_IDENTITY_ASSERTER) token when policies are configured for this.
10g WebGate: Sets and returns OAM_REMOTE_USER or OAM_IDENTITY_ASSERTION headers in the request when policies are configured for this.
mod_weblogic forwards requests as directed by its configuration.
Note: mod_weblogic is the generic name of the WebLogic Server plug-in for Apache For Oracle HTTP Server 11g, the name of this plug-in is mod_wl_ohs. (in OHS server)
7) WebLogic Server security service invokes the Oracle Access Manager Identity Asserter which is configured to accept tokens of type "OAM_REMOTE_USER" (or "OAM_IDENTITY_ASSERTER"). The Identity Asserter initializes a CallbackHandler with the header. In addition, the Identity Asserter sets up NameCallback with the username for downstream LoginModules.
8) Oracle WebLogic Security service authorizes the user and allows access to the requested resource. (This resource is the Application which was deployed on WebLogic server).
9) A response is sent back to the reverse proxy Web server.
10) A response is sent back to the browser


Comments
Post a Comment