Second factor authentication with Oracle Access Manager
OAM 11gR2PS3 comes with the Adaptive Authentication services that provides multi-factor authentication capability. (second factor authentication is an example of multi-factor authentication) In earlier to OAM 11gR2 versions, one had to separately install OAAM product to get the Adaptive Authentication services/functionality, read here. However with 11gR2 PS2 and now in PS3 versions OAM includes the Adaptive Authentiation service.
What is Adaptive Authentication Service?
This services comes as part of the OAM since 11gR2 PS2. It provides the OTP (One Time Password) authenticator functionality.
What does Adaptive Authentication Service do?
It provides two factor authentication or rather multifactor authentication. For example, the Adaptive Authentication Service provides the second authentication, in addition to username/password that is already provided by OAM.
Oracle Adaptive Access Manager helps organizations prevent fraud and misuse by strengthening existing authentication flows, evaluating the risk of events as they happen and providing risk-based interdiction mechanisms such as multi-factor out-of-band authentication.
Why is it required, what is the use case?
It can be used to provide an additional or step-up authentication for for applications. For example sensitive applications may require an additional step to verify the identity of a user.
Configuring Adaptive Authentication Service (from Oracle Fusion Middleware (OFMW) Administrator Guide)
Oracle Access Manager, OAM provides the username/password authentication to applications. The Oracle Adaptive Authentication service provides the second factor of authentication. If your requirement is to add another authentication, i.e Second factor authentication, then you use the capability of Adaptive Authentication. This multifactor authentication involves more than one stage of verifying the identity of a user attempting to access services/application. The first factor of authentication is the username and password and the additional authentication is provided by adding a OTP, One Time Password step or a Push Notification step. Here is the LINK to Oracle docs for Adaptive Authentication Service
On the OAM console you enable the Adaptive Authentication Service (this services has to explictly enabled and licensed for use)
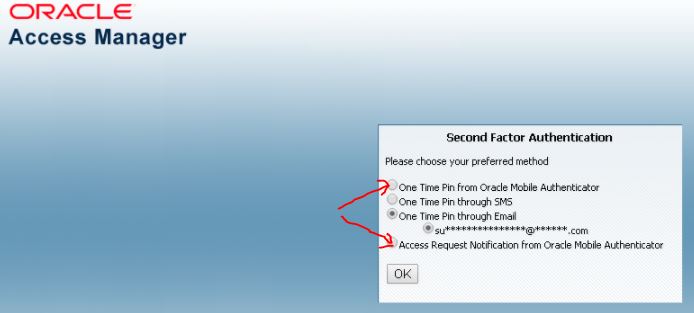
The Adaptive Authentication Service that provides the additional factor of authentication can be a One Time Pin (OTP) or an Push Notification (Access Request Notification). After the user successfully authenticated with usename/password, the Second Factor Authentication page is displayed from which the user selects the preferred method of this second authentication - which can be either of the following options - (1) OTP from OMA (Oracle Mobille Authenticator), (2) OTP through SMS, (3) OTP through Email, or (4) Push Notification from OMA.
Note: You require to download/configure the Authenticator app to the mobile device (e.g. Apple iPhone, or a Android based mobile device) in order to use the two options shown below, (1) OTP from OMA, or (2) Push Notification (Access Request Notification from OMA). For these two options, the OAM server works with the OMA (Oracle Mobile Authenticator) to provide the second factor authentication.
In advance of using the OTP from OMA or Access Request Notification from OMA options, a user must download a supported authenticator app to the mobile device (for example download the Oracle Mobile Authenticator app to an Apple iPhone or an Android based mobile device) and configure it by clicking a link provided by the Access Manager administrator. (The OMA app is not needed if using the OTP through Email or OTP through SMS options.)
If you need complete integration of user self registration with your Oracle Identity Management deployment with step up authentication, either through OTP, SMS, Push Notification or OTP through email, then OAM, OIM and OAAM need to be integrated (Read here). These three products when integrated will provide you the full user self service from registration, to password management capability to the login/access to applications with multi-factor authentication. OAAM provides user login to second factor authentication, challenge and registration, self-service flows, OIM provides user provisioning, add, modify, delete users and managing password flows for change password, reset password, OAM provides authentication ad authorization of users.
The following steps should be completed in order to achieve full integration of OAM,OIM,OAAM
Integration of OAM with OIM
Configure LDAP sync
Integration of OAM and OAAM
Finally Integration of OAAM and OIM
---------------------------------------------------------------------------------------------------------------------
Oracle Mobile Authenticator
Oracle Mobile Authenticator enables you to securely verify your identity by using your mobile device as an authentication factor. The app generates one-time passcode for login. Or it can receive notifications for login, which can be approved with a simple tap. When this authentication is used on top of username-password, it adds an additional layer of security that is essential for today's online applications.
Features:
- Generate one time passcode even when the device is offline
- Push Notification based approval
- Fingerprint or App PIN for app protection
- Set up via QR code, Config URL, or by entering key manually
- Multiple account support
- Generate OTP for other applications that make use of passcodes as per RFC 6238
What is Adaptive Authentication Service?
This services comes as part of the OAM since 11gR2 PS2. It provides the OTP (One Time Password) authenticator functionality.
What does Adaptive Authentication Service do?
It provides two factor authentication or rather multifactor authentication. For example, the Adaptive Authentication Service provides the second authentication, in addition to username/password that is already provided by OAM.
Oracle Adaptive Access Manager helps organizations prevent fraud and misuse by strengthening existing authentication flows, evaluating the risk of events as they happen and providing risk-based interdiction mechanisms such as multi-factor out-of-band authentication.
Why is it required, what is the use case?
It can be used to provide an additional or step-up authentication for for applications. For example sensitive applications may require an additional step to verify the identity of a user.
Configuring Adaptive Authentication Service (from Oracle Fusion Middleware (OFMW) Administrator Guide)
Oracle Access Manager, OAM provides the username/password authentication to applications. The Oracle Adaptive Authentication service provides the second factor of authentication. If your requirement is to add another authentication, i.e Second factor authentication, then you use the capability of Adaptive Authentication. This multifactor authentication involves more than one stage of verifying the identity of a user attempting to access services/application. The first factor of authentication is the username and password and the additional authentication is provided by adding a OTP, One Time Password step or a Push Notification step. Here is the LINK to Oracle docs for Adaptive Authentication Service
On the OAM console you enable the Adaptive Authentication Service (this services has to explictly enabled and licensed for use)
The Adaptive Authentication Service that provides the additional factor of authentication can be a One Time Pin (OTP) or an Push Notification (Access Request Notification). After the user successfully authenticated with usename/password, the Second Factor Authentication page is displayed from which the user selects the preferred method of this second authentication - which can be either of the following options - (1) OTP from OMA (Oracle Mobille Authenticator), (2) OTP through SMS, (3) OTP through Email, or (4) Push Notification from OMA.
Note: You require to download/configure the Authenticator app to the mobile device (e.g. Apple iPhone, or a Android based mobile device) in order to use the two options shown below, (1) OTP from OMA, or (2) Push Notification (Access Request Notification from OMA). For these two options, the OAM server works with the OMA (Oracle Mobile Authenticator) to provide the second factor authentication.
In advance of using the OTP from OMA or Access Request Notification from OMA options, a user must download a supported authenticator app to the mobile device (for example download the Oracle Mobile Authenticator app to an Apple iPhone or an Android based mobile device) and configure it by clicking a link provided by the Access Manager administrator. (The OMA app is not needed if using the OTP through Email or OTP through SMS options.)
If you need complete integration of user self registration with your Oracle Identity Management deployment with step up authentication, either through OTP, SMS, Push Notification or OTP through email, then OAM, OIM and OAAM need to be integrated (Read here). These three products when integrated will provide you the full user self service from registration, to password management capability to the login/access to applications with multi-factor authentication. OAAM provides user login to second factor authentication, challenge and registration, self-service flows, OIM provides user provisioning, add, modify, delete users and managing password flows for change password, reset password, OAM provides authentication ad authorization of users.
The following steps should be completed in order to achieve full integration of OAM,OIM,OAAM
---------------------------------------------------------------------------------------------------------------------
Oracle Mobile Authenticator
Oracle Mobile Authenticator enables you to securely verify your identity by using your mobile device as an authentication factor. The app generates one-time passcode for login. Or it can receive notifications for login, which can be approved with a simple tap. When this authentication is used on top of username-password, it adds an additional layer of security that is essential for today's online applications.
Features:
- Generate one time passcode even when the device is offline
- Push Notification based approval
- Fingerprint or App PIN for app protection
- Set up via QR code, Config URL, or by entering key manually
- Multiple account support
- Generate OTP for other applications that make use of passcodes as per RFC 6238


Comments
Post a Comment